'How to Recover from the Log4j Supply Chain Attack with Ilkka Turunen' by hackernoon hackernoonpodcast supplychainattacks
[00:00:00] Amy Tom: Hello hackers. This is the HackerNoon podcast. And my name is Amy Tom, your podcast host, and very best friend. I've got a little PSA for you about the times that we're living in and technology. I just started reading this very average romance, crime novel. It's called the Bitcoin Widower. And it's about a woman who meets a man on Tinder who owns a Bitcoin exchange, and he goes missing.
[00:01:14] Ilkka Turunen: Um, I'm pretty sure someone actually faked their death to get away with bitcoin. So yeah, that's the world we live in. and so what I'm responsible really is. running the teams that actually engage with, people thinking about our tools and, uh, you know, implementing them and just help them, make sure that they, put it over there, get it built correctly, you know, get it designed correctly.
[00:03:30] Ilkka Turunen: Yeah, there's just two, there's Brian Fox who our co-founder and CTO, he's the actual CTO and an amazing tech God. And then there's me. Who goes, all right. That's uh, that's how you say to the world, like here's how we act, what he actually means to the people that have to implement this thing.
It meaningfully, when we're making these product and investment decisions really just helps, the company do the right moves and, built the right thing so that, six months down the line, the customers don't scratch their heads and go what's this, then once you build it. But actually you might not be thinking about it at the proper scale. So we're helping you to figure that one out. And as, as we have these conversations, like, no, company's the same. it feels like everybody thinks about the same things and thinks about things in the same way.
So w we try and take kind of a. Data oriented way of making that decision. obviously mixed in with our good senses as well. So really it's, it's all in all in everything, one day I might just be, doing a white boarding session next day, I might be talking to executives about how to measure a medical.
Ceremony of having to book a room and figuring out who gets the coffees in and, and things like that. on the other hand, yeah. It, it certainly did it change because, you sometimes hear the most honest feedback after the meeting in the whole, on the way out. and, those sorts of moments you now have to think about, you know, how do you make sure that, you know, we're, we're running the meeting in a way that allows people to express that.
So, customers are starting to pay attention to it. and they speed and also, uh, added onto, by the fact that governments have started issuing, decrease, you know, the Biden administration putting out. The executive order about dealing with the supply chain. So it is certainly, increased activity, quite a lot.
And in there, there's an entire segment about a software supply chain security. And one of the things that they say. Is that, they will come out with minimal sulfur bill of materials standards, and they will require every company that sells software to the U S government to provide a list of ingredients, so to speak.
[00:11:55] Ilkka Turunen: Yeah to a certain degree. I mean, it, it depends on how deep you want to go, but the actual fundamentals of this come from the sixties. You know, you'll have to drive your car and they'll do something, you know, change the airbags or whatever. If I asked anyone writing software today, could you do. Well after log4J, I think more companies will say yes, but they really, even six months ago I wrote, it was like, what do you even mean?
The piece of, um, you know, Java, for example, easy to see 150 300 pieces of what a third party components, uh, in their JavaScript. You can probably draw zero at the end. You know, if you've ever heard of dependency help, that's what they do. And that sort of, uh, that sort of sphere. Um, the amount of open source is less meaningful.
And now when you think about load for J today, most companies that I talk to, they're kind of getting to that sort of hangover phase off while we had a big. Fire braille. We kind of figured out to mitigate it, but there's this long tail of stuff that probably has it, you know, he didn't even, you know, as a part of another component or something like that.
You're looking through the list and saying, Hey, wait a minute. That has a known vulnerability. It's like a 10 hour. Don't don't accept it. Just like leave it at the door. Cause that's like a ton of work off of your desk, like immediately. Sometimes lead you down a hellish rabbit hole. And most people go, you know what, as long as it works and I don't get breached, that's probably okay. and, that's the kind of track that a lot of people fall into. It's like, learning to wash your hands before surgery.
[00:19:12] Ilkka Turunen: that's the typical, symptom of, having to come up with a new, discipline. I think we're starting to realize, right. Is that it isn't just like, Hey, I should be mining about everything. I think it's really a new kind of muscle that every software company has to, has to develop because you're absolutely right.
Thousands, if not millions of people, and even if it's off for just a day or two, that's enough of a downstream effect. That's unfortunately the reality of the way we write software today. And it certainly something that that's causing a little bit of a heartache and then, It. There's no such thing as a hundred. Secure security. Like, there's just absolutely. If somebody tells you that, just walk away and go somewhere else, but that's a complete lie. Um,
Are you, are you willing to do that? And that often gets folks scratching heads. So it's, it's not even just about security. Always. It can just be like, well, You've got 10 teams and every team uses a different front framework. Why is that? Like just asking sort of very fundamental questions and people go, well, my devs choose their own tools.
Java code or Android code or anything that's related to Java like Scala, typically the third-party stuff comes from us. We run the servers and the CDN that, the provides them with the dependencies. And when look for Jay happened, we actually ran the numbers. Look for Jay Is in the top 0.03% most popular open source component.
Like any, anyone can do it. That's where the danger. So it happens. So, when Jake came out there were like people put punching it in, in their Teslas, the attack string and getting like responses back, knowing that, Hey I could have done this. And that's why actually most governments tilt their at teams that they have until about Christmas.
and that's what made it so scary and widespread it's because it's not just the code that the software, the companies wrote themselves. It's any piece of Java software that they've ever bought in for Gordon to patch runnings in some server somewhere that might have Nick broker access, that's the liable to that attack.
So all of a sudden everybody's minds are focused on. That single method of attack. And, it's like somebody finding a very fundamental flaw in the logic of how that code is written. It, it spreads out and that's really the next dangerous, like, it wasn't actually just that thing. So it's, the danger is still very much out there. And I think. Just the mathematics, you know, 40% of every new bill still has an old version of log for J you know, that there's a lot of a surface up or for them.
And yet still to this day, it's it's. The kind of state of aligning though, there's various in countries like generally English speaking countries tend to do a little bit better. I think it's because all the tech companies are, from those countries and there's a lot of PSA's on them, but there are countries still in the world.
So it takes two seconds per build and it makes a huge dent further down the line, for you the second step then is to start thinking about, across teams or, if I just talked to my colleague in the next team over, or, talk to my colleagues in, in, in America, do they even use the same libraries that I do if they don't?
If you do that, that's going to go a long way to actually just mitigating a lot of these sort of longer tail risks, that might happen. And then when something new happens, like often what we like to ask customers is, Hey, if I told you there's another log for J and it's going to come up tomorrow, what would you do?
United States Latest News, United States Headlines
Similar News:You can also read news stories similar to this one that we have collected from other news sources.
 As pandemic supply chain problems subside, conflict in Ukraine could cause other global supply issuesShipping experts worry if the war persists, companies with ships that move around the region face safety concerns.
As pandemic supply chain problems subside, conflict in Ukraine could cause other global supply issuesShipping experts worry if the war persists, companies with ships that move around the region face safety concerns.
Read more »
 Ford bedeviled by supply-chain problems | Car News | Auto123Ford dealers got some frustrating news from the automaker this weekend, as ongoing supply-chain issues continue to affect deliveries and inventories.
Ford bedeviled by supply-chain problems | Car News | Auto123Ford dealers got some frustrating news from the automaker this weekend, as ongoing supply-chain issues continue to affect deliveries and inventories.
Read more »
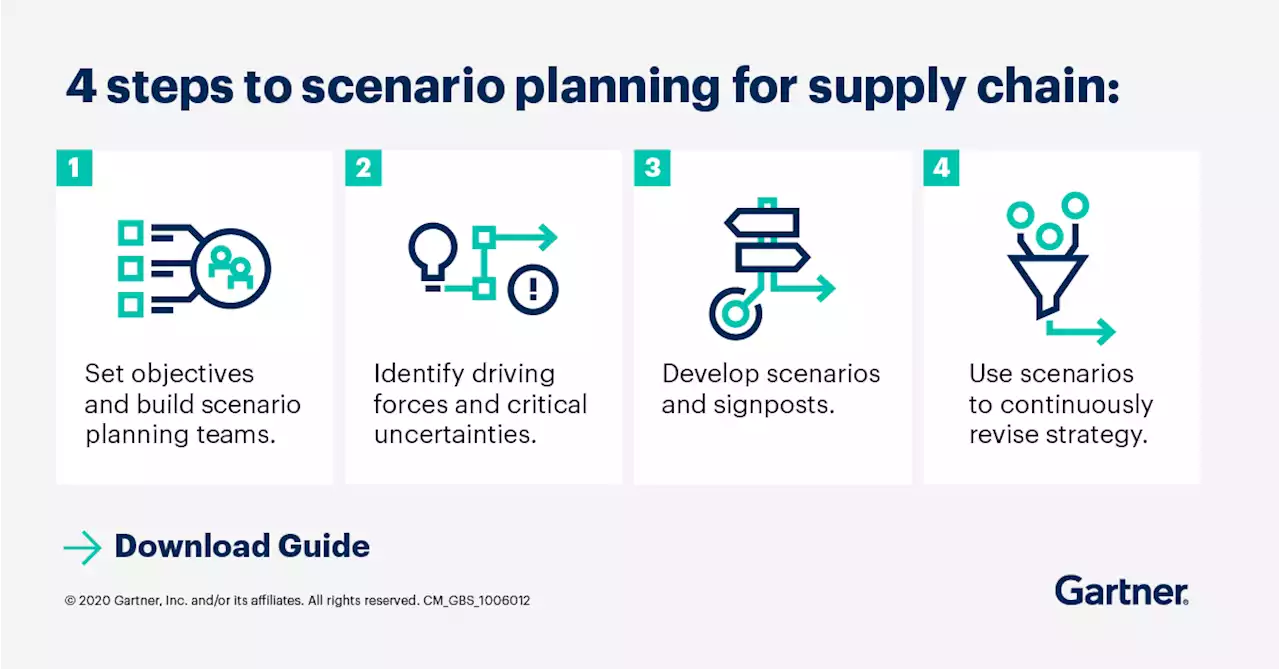 Step-by-Step Guide to Supply Chain Scenario PlanningScenario planning has never been more important to supply chain resilience and commercial success. Get a step-by-step action plan in Gartner_SC's Scenario Planning for Supply Chain guide 👉 GartnerSC SupplyChainManagement
Step-by-Step Guide to Supply Chain Scenario PlanningScenario planning has never been more important to supply chain resilience and commercial success. Get a step-by-step action plan in Gartner_SC's Scenario Planning for Supply Chain guide 👉 GartnerSC SupplyChainManagement
Read more »
 Saskatchewan government cites supply chain issue, extends crop insurance deadlineFarmers in the province will have a little more time to enrol for crop insurance.
Saskatchewan government cites supply chain issue, extends crop insurance deadlineFarmers in the province will have a little more time to enrol for crop insurance.
Read more »
 What Closure of Manufacturing Facility in China Could Mean for Tech Supply ChainChina has temporarily shut down one of the world’s largest electronics manufacturing facilities to fight a new COVID-19 spike, possibly triggering another supply chain issue that could hit the Bay Area hard.
What Closure of Manufacturing Facility in China Could Mean for Tech Supply ChainChina has temporarily shut down one of the world’s largest electronics manufacturing facilities to fight a new COVID-19 spike, possibly triggering another supply chain issue that could hit the Bay Area hard.
Read more »
 Saskatchewan government cites supply chain issue, extends crop insurance deadlineICYMI: Saskatchewan government cites supply chain issue, extends crop insurance deadline
Saskatchewan government cites supply chain issue, extends crop insurance deadlineICYMI: Saskatchewan government cites supply chain issue, extends crop insurance deadline
Read more »
