Learn about definite misuses, dependency impacts, rule violations, and insights into security vulnerabilities across cryptographic libraries.
Authors: Anna-Katharina Wickert, Technische Universität Darmstadt, Darmstadt, Germany ; Lars Baumgärtner, Technische Universität Darmstadt, Darmstadt, Germany ; Florian Breitfelder, Technische Universität Darmstadt, Darmstadt, Germany ; Mira Mezini, Technische Universität Darmstadt, Darmstadt, Germany . Table of Links Abstract and 1 Introduction 2 Background 3 Design and Implementation of Licma and 3.1 Design 3.2 Implementation 4 Methodology and 4.
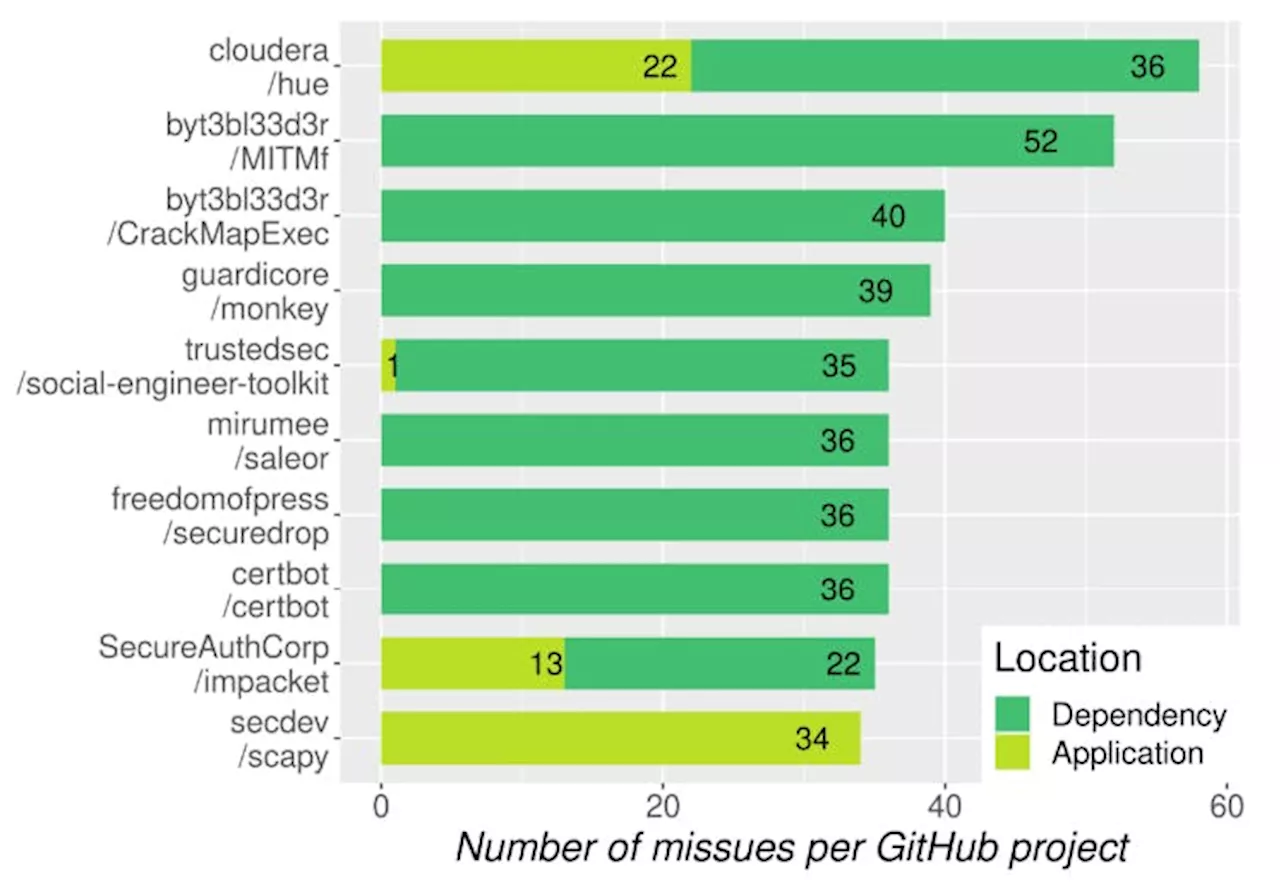
is definitely violated by the respective API call. We identified 85 definite misuses which could be identified within one class file and thus are local. The remaining 1,416 misuses are potential misuses. 5.1.1 Dependencies. From the 1,501 misuses, only 7.00 % are within the application code and not in dependencies. These misuses are within 14.81 % of the applications with at least one misuse. The remaining misuses are found in dependencies and can be reduced to 290 unique misuses.
As discussed in Section 3.1, we distinguish between potential and definite misuses. While a potential misuse requires a manual inspection to decide whether it is harmful, a definite misuse indicates that the analysis was able to resolve the respective crypto parameter. Thus, we know that a rule of
United States Latest News, United States Headlines
Similar News:You can also read news stories similar to this one that we have collected from other news sources.
 LICMA's Analysis of Crypto API Misuses in Python Apps: Findings and Future DirectionsExplore insights from LICMA's empirical study on crypto misuses in Python apps, highlighting the impact of user-friendly API design and of hybrid analysis.
LICMA's Analysis of Crypto API Misuses in Python Apps: Findings and Future DirectionsExplore insights from LICMA's empirical study on crypto misuses in Python apps, highlighting the impact of user-friendly API design and of hybrid analysis.
Read more »
 Python Crypto API Misuses in the Wild: Analyzing Threats to ValidityLearn about the limitations in current analysis tools and frameworks, impacting the accuracy and scope of findings in crypto misuse studies.
Python Crypto API Misuses in the Wild: Analyzing Threats to ValidityLearn about the limitations in current analysis tools and frameworks, impacting the accuracy and scope of findings in crypto misuse studies.
Read more »
 A Comparative Analysis of Crypto API Misuses Across Programming LanguagesExplore a comparative analysis of crypto security across Python, Java, and C based on empirical studies.
A Comparative Analysis of Crypto API Misuses Across Programming LanguagesExplore a comparative analysis of crypto security across Python, Java, and C based on empirical studies.
Read more »
 How We Analyzed Crypto API Misuses in 895 GitHub ProjectsDiscover the methodology behind analyzing crypto misuses in Python and MicroPython projects from GitHub and curated MicroPython repositories.
How We Analyzed Crypto API Misuses in 895 GitHub ProjectsDiscover the methodology behind analyzing crypto misuses in Python and MicroPython projects from GitHub and curated MicroPython repositories.
Read more »
History of Crypto: Crippling inflation, rising debt, and the evolving crypto landscapeExplore the history of crypto amidst crippling inflation, rising US debt, and transformative events like FTX's collapse and Ethereum's proof-of-stake shift. Dive into the evolving landscape of the cryptocurrency industry.
Read more »
History of Crypto: The future of crypto exchanges, regulatory battles, and governanceExplore the aftermath of the FTX exchange collapse, regulatory crackdowns, and the evolution of crypto governance. Discover how industry shifts shape the future of exchanges and investor safety
Read more »